
Why Do You Need a VA Cybersecurity Strategy?
As you start working with a remote executive assistant, the importance of taking certain cybersecurity measures has never been more critical. Delegating tasks to EAs often involves granting access to sensitive information and confidential systems, making it essential to protect against potential cyber threats. Cybersecurity breaches can lead to significant financial losses, damage to reputation, and legal complications. In fact, according to recent IBM reports, the global cost of data breaches and financial losses increased by up to 5 million USD in the year 2022 and it’s forecasted that the breach costs will increase by up to $8 Trillion globally. This article aims to guide businesses in developing and implementing effective virtual assistant cybersecurity strategies tailored to working with virtual assistants. We’ll provide practical advice and best practices for ensuring data protection and minimizing risks associated with remote work arrangements.
Types of Cyber Risks When Hiring Virtual Assistants
1. Phishing Attacks and Malware:
Phishing attacks are a common threat faced by businesses using virtual assistants. Cybercriminals often disguise themselves as legitimate entities to trick new EAs into divulging sensitive information such as login credentials or financial details. These attacks usually come in the form of emails or messages containing malicious links or attachments, which, when clicked, can install malware on the system. This malware can cause significant harm, including data theft, corruption, or unauthorized access to company systems.
2. Data Breaches and Unauthorized Access:
Data breaches can occur when unauthorized individuals gain access to sensitive company information. This can happen if an EA's login credentials are compromised or if virtual assistant security protocols are not adequately enforced. Unauthorized access can lead to the exposure of confidential data, which can be sold on the dark web or used for malicious purposes.
3. Insider Threats from a Negligent VA Cybersecurity Strategy:
Insider threats pose a significant risk to businesses employing virtual assistants. A remote executive assistant may intentionally or unintentionally compromise data security. Malicious insiders might exploit their access for personal gain, while negligent EAs may accidentally expose sensitive information through careless actions. These threats definitely cause the need for strict security policies and ongoing monitoring to detect and mitigate any potential risks from within.
Potential Consequences of Security Breaches
1. Financial Losses and Reputational Damage:
Security breaches can lead to substantial financial losses due to fraud, theft, or the cost of remedial actions. Businesses may face downtime, loss of customer trust, and decreased sales as a result of compromised data. Additionally, reputational damage can have long-term impacts, as customers and partners may lose confidence in the company’s ability to protect their information, leading to further financial repercussions.
2. Legal and Compliance Issues:
Businesses are subject to various data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). A security breach involving virtual assistants can result in non-compliance with these regulations, leading to legal consequences and hefty fines. Companies must ensure that their cybersecurity strategies align with legal requirements to avoid legal liabilities and ensure the protection of customer data.
Developing a VA Cybersecurity Strategy
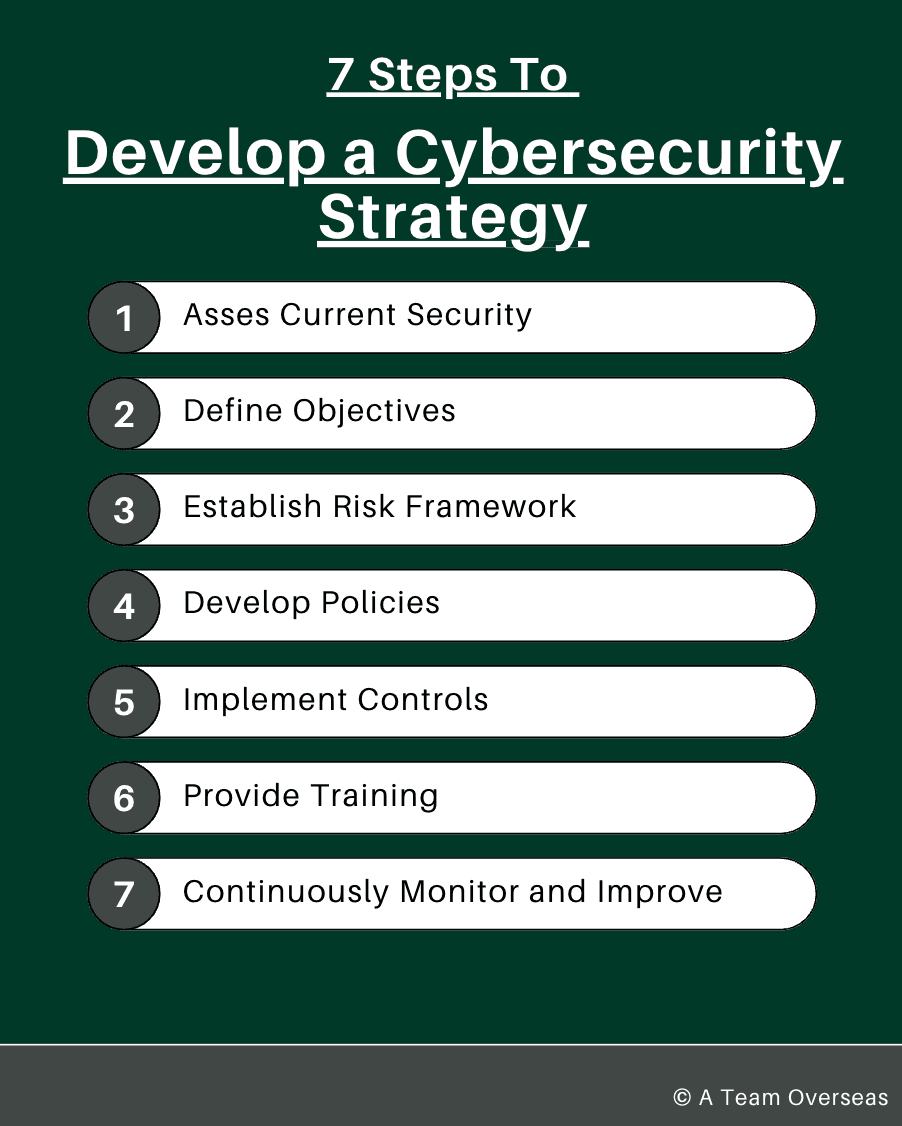
1. Assessing Your Security Needs:
The first step in developing an EA cybersecurity strategy is to understand the scope of access your virtual assistants have. Identify the types of data they handle, such as customer information, financial records, or proprietary business data. Determine which systems, applications, and databases they need to access to perform their tasks as you determine what to delegate to your remote executive assistant.
Assess the potential consequences of a security breach involving virtual assistants. Consider how a breach could affect your operations, finances, reputation, and legal standing. By evaluating the impact, you can prioritize the protection of critical assets and implement measures that align with the level of risk associated with each type of data or system.
2. Establishing Security Policies and Protocols:
Develop a detailed virtual assistant cybersecurity policy that outlines the responsibilities and expectations for virtual assistants. This policy should cover data handling practices, acceptable use of company systems, and procedures for reporting security incidents. Ensure that EAs are aware of the policy and understand their role in maintaining security.
Implement the principle of least privilege by granting EAs only the access necessary to perform their tasks. Define access levels and permissions based on their roles and responsibilities. Use role-based access control (RBAC) to manage and monitor access rights effectively.
3. Leverage Tools and Technologies for Enhanced Security:
Use password managers to generate and store complex, unique passwords for each system and application. This reduces the risk of password reuse and unauthorized access. Implement two-factor authentication (2FA) to add an extra layer of security. 2FA requires a second form of verification, such as a code sent to a mobile device, making it more difficult for attackers to gain access even if they obtain a password.
It’s bets if you require your EA to use virtual private networks (VPNs) when accessing company systems and data remotely. VPNs encrypt internet traffic, protecting sensitive information from interception by cybercriminals. Use secure communication channels, such as encrypted email services and messaging apps, to protect data during transmission and ensure that conversations remain confidential.
Finally, you should also encrypt sensitive data both at rest and in transit to prevent unauthorized access. Use strong encryption standards to protect data stored on company servers and devices. Ensure that data is encrypted when transmitted over networks, especially public or unsecured ones. Encryption safeguards data integrity and confidentiality, providing an essential layer of protection against cyber threats.
4. Learn How to Address Security Breaches
VA Cybersecurity Strategy: Steps to Take in Case of a Security Breach
-
Immediate Containment and Assessment:some text
- As soon as a breach is detected, isolate affected systems to prevent further unauthorized access or damage.
- Conduct a rapid assessment to determine the scope and nature of the breach, identifying affected data and systems.
-
Notification of Incident Response Team:some text
- Alert your incident response team, which should include IT personnel, security experts, and relevant managers.
- Ensure that everyone understands their roles and responsibilities in the response process.
-
Eradication and Recovery:some text
- Remove malicious software, unauthorized users, or other threats from affected systems.
- Restore systems from secure backups and verify the integrity and virtual assistant security of data and applications before bringing them back online.
-
Documentation and Evidence Gathering:some text
- Document all aspects of the breach, including the timeline, affected systems, and actions taken.
- Preserve evidence for potential legal or forensic investigations.
-
Review and Report:some text
- Conduct a detailed review of the incident to understand how the breach occurred and the effectiveness of the response.
- Prepare a report for internal use and regulatory compliance, if required.
5. Start Communicating Breaches to Stakeholders and Authorities:
-
Internal Communication:some text
- Inform relevant internal stakeholders, including senior management, of the breach and its potential impact.
- Provide regular updates as the situation evolves and resolves.
-
External Communication:some text
- Notify affected customers and partners promptly if their data has been compromised, explaining the breach and steps taken to address it.
- Communicate with regulatory authorities if required by law, providing necessary details and documentation.
6. Updating Security Policies and Training:
Make sure to double-check your VA cybersecurity strategy and policies and protocols to address identified weaknesses and prevent similar breaches in the future. Update your virtual assistant cybersecurity training programs for virtual assistants and other employees, incorporating lessons learned from the incident to enhance awareness and preparedness. Regularly test and refine your incident response plan to ensure its effectiveness and adapt it to emerging threats and evolving business needs.
Ready To Hire a Remote Executive Assistant With Cybersecurity Support?
Prioritizing a VA cybersecurity strategy will help you proactively mitigate potential risks and take care of your business, leaving you better positioned to handle potential threats, and minimize financial losses and reputational damage. As your EA partnership continues to evolve, staying ahead of cyber risks is vital for maintaining a secure and resilient work environment and ensuring long-term success. Now, if you’re ready to start working with a remote executive assistant and would like to have as much support throughout the engagement, we can help. At A Team Overseas, we offer EA subscription services with founder-led guidance to ensure you leverage our years of experience, including our VA cybersecurity strategy and delegation workflow. Contact us today to get started and hire an EA!